Security
‘Rasputin’ Hacker Targets 60 Universities, Government Agencies
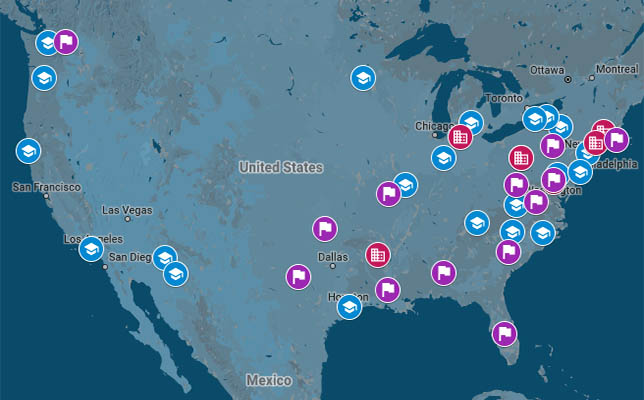
Image Credit: Recorded Future.
More than 60 universities and government agencies in the United States and the United Kingdom have been attacked by a well-known international hacker. Dubbed “Rasputin,” the Russian-speaking “notorious financially-motivated cyber criminal [who] continues to locate and exploit vulnerable web applications via a proprietary SQL injection tool” is behind the latest round of attacks, according to intelligence firm Recorded Future.
Commonly used SQL injection (SQLi) scanners including Havij, Ashiyane SQL Scanner, SQL Exploiter Pro, SQLI Hunter and countless others are used to automate the identification and exploitation of vulnerable websites and associated databases, the firm explained in a blog post. Over the last few months, Rasputin was able to breach databases at prominent universities, as well as federal, state and local governments using an SQLi tool that he developed himself.
“Financial profits motivate actors like Rasputin, who have technical skills to create their own tools to outperform the competition in both identifying and exploiting vulnerable databases,” Recorded Future wrote. “North American and Western European databases contain information on customers or users that are historically valued at a premium in the underground economy. Buyer demand typically centers on access to American, Canadian or U.K. database access.”
Recorded Future first discovered criminal activity targeting government organizations back in December. On Dec. 28, Recorded Future contacted the Federal Bureau of Investigation and the Department of Homeland Security. But SQLi attacks are nothing new, according to the firm, and have been around for more than 15 years since databases first appeared on the internet. Large organizations often fall prey to SQLi which is preventable, the firm wrote, with coding best practices. “Until organizations have an incentive (carrots or sticks) to properly audit internal and vendor code before production use, this problem will continue into the foreseeable future.”
The U.S. universities that were attacked are:
To see the complete list of affected universities and governments, visit the Recorded Future site here.
About the Author
Sri Ravipati is Web producer for THE Journal and Campus Technology. She can be reached at [email protected].

