DMARC Study: Most Higher Ed Domains Not Protecting E-mail Security Fully
- By Kristal Kuykendall
- 03/09/23
New research shows that an overwhelming majority of education institutions in the United States have incorrectly configured e-mail security settings and as a result are more susceptible to phishing and spoofing threats.
The report from e-mail security provider EasyDMARC reviewed the security policies of .edu e-mail domains, which are assigned to 1,930 U.S. higher education institutions. The researchers found that only 152 — or a mere 7.8% — of the country’s .edu domains have correctly implemented and configured security policies to flag, report, and remove outbound phishing e-mails.
The survey reviewed the deployment of the Domain-based Message Authentication, Reporting and Conformance (DMARC) standard among .edu domains, first published in 2012. The standard enables the automatic flagging and removal of receiving e-mails that are impersonating senders’ domains, which EasyDMARC described as “a crucial way to prevent outbound phishing and spoofing attempts.”
While 58% of U.S. .edu domains had implemented the DMARC standard, more than 9 in 10 were not completely implemented in a manner that deploys all of DMARC’s capabilities, EasyDMARC said in its report, “DMARC Guide for Education IT Staff.”
Key Findings of the EDU Domain Study
Among the .edu domains that had implemented DMARC, 848 or 76% were using DMARC only to monitor outgoing e-mails impersonating legitimate domains.
-
199 or 18% of DMARC-using .edu domains were only slightly more complete in their implementation, having also set their policies to send impersonating e-mails to quarantine.
-
152 institutions — 7.8% of all .edu domains, equaling 14% of DMARC-using .edu domains — had DMARC set to automatically reject site e-mails impersonating their domain.
The institutions not using the full DMARC capabilities “leave users vulnerable to still receiving phishing e-mails … and creates a substantial risk for ransomware attacks, fraud, and data breaches,” said the report.
“It’s very concerning to see that less than one in ten U.S. higher ed institutions have adopted adequate protection against (phishing and spoofing) attacks by adequately implementing a DMARC solution,” said EasyDMARC CEO Gerasim Hovhannisyan.“With many organizations moving to cloud-based e-mail ecosystems, it’s likely that many educational institutions are finding it difficult to find a way to implement DMARC that can operate seamlessly alongside their SaaS solution stack. For vendors and service providers to educational institutions, these findings should be a wake-up call regarding the massive security gap that needs to be filled with cloud-native DMARC solutions.”
The report noted that in the first six months of 2022, the education and research sector saw a 44% increase in cyberattacks globally, and according to Checkpoint’s 2022 Cyber Attack Trends Mid-Year Report, education was the most targeted industry for the period.
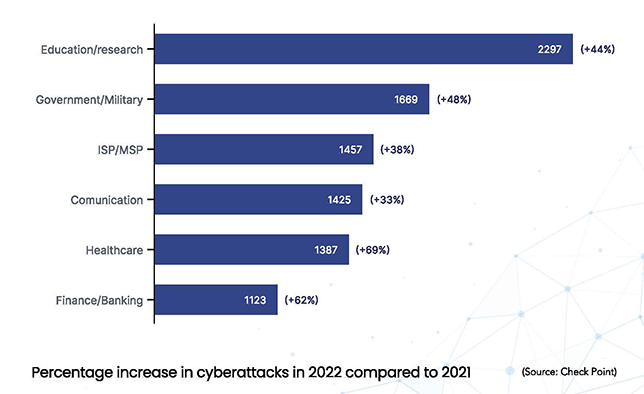 The Checkpoint data also shows that e-mail-delivered attacks comprised 89% of all “in the wild” cyberattacks during that period. Also widely seen were malicious “Microsoft documents” attachments delivering malware — representing 61% of all malware attacks.
The Checkpoint data also shows that e-mail-delivered attacks comprised 89% of all “in the wild” cyberattacks during that period. Also widely seen were malicious “Microsoft documents” attachments delivering malware — representing 61% of all malware attacks.
What is DMARC and Why Does It Matter?
DMARC instructs receiving servers on how to deal with unauthorized e-mails from a particular domain. The protocol allows IT admins to “determine whether an unauthorized e-mail (purporting to be legitimate) should land in a receiver’s inbox, spam folder, or not be accepted at all,” explained EasyDMARC’s report. “The protocol stops malicious actors from impersonating employees or students with fake organizational e-mail addresses while protecting recipients from fraudulent scams.”
Proactive IT professionals should be fully deploying DMARC, the report said, which might take anywhere from a few weeks to several months. This also requires continuous maintenance, EasyDMARC said.
“Setting up the record in your DNS might create an illusion of being protected while bad actors are still lurking in your domain environment,” the report warned. “DMARC desertion is a common practice among security teams. Even if you’ve finally reached the ‘reject’ policy, periodical maintenance of your domain infrastructure, including sending source reviews and record updates, should be on your to-do list.”
DMARC Adoption in Education
EasyDMARC research showed that out of 12,050 randomized .edu domains studied worldwide, just 401 have reached “reject.” In addition to the domains that use the p=reject policy, the researchers classified the samples of domains using the following criteria:
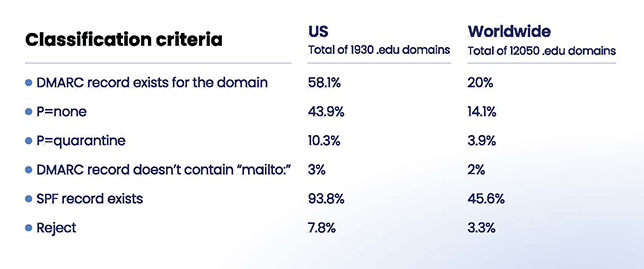
In the U.S. sample, the number of .edu domains with a DMARC record is 1,122 or 58%. However, filling in the empty slot for the DMARC record is not enough to protect an organization’s e-mail infrastructure, EasyDMARC said in its report.
Almost 94% of the domains studied have “successfully deployed the first step of e-mail authentication – they have an active SPF record,” the report said. “Still, let’s not forget DMARC works based on SPF and DKIM protocols.”
Setting up SPF is only one-third of the e-mail authentication journey, according to the report.
In the research sample, 848 .edu domains have set their DMARC to “monitoring mode” (p=none), while only 199 worked on advancing it to p=quarantine. “This leaves the door wide open to malicious actors and costly cyberattacks,” the report said.
Thorough DMARC implementation and policies have a number of benefits besides protecting from the “when, not if” phishing and spoofing attacks, the report said:
-
Establishes infrastructure visibility: DMARC “lets you know exactly what’s happening in your e-mail domain infrastructure,” the report said.
-
Improves e-mail deliverability: E-mail deliverability is a “side effect of an increased domain reputation rather than a direct technical outcome of DMARC implementation,” the report said.
-
Protects data and stakeholders: When unauthorized e-mails are blocked from being delivered, “no spoofing or phishing attack can reach a recipient,” the report said. “This mitigates data theft and other cyberattacks.”
-
Nurtures trust and brand reputation: “Taking action to prevent impostors from posing as your organization improves brand image ... and increases trust among e-mail contacts inside and outside your organization,” said the report.
About the Author
Kristal Kuykendall is editor, 1105 Media Education Group. She can
be reached at [email protected].