Snapshot: College-Age Kids Come Well Equipped
Americans of traditional college age are loaded up with personal devices and have the highest rate of ownership of mobile phones among all age groups, according to a new report released this week by the Pew Research Center's Internet & American Life Project.
According to the research, published in the study "Younger Americans' library habits and expectations," 94 percent of Americans aged 18 to 24 own a cell phone (either a smart phone or feature phone). That's slightly higher than high school-aged kids, 93 percent of whom own a mobile phone, and the next age group up (25–29), 91 percent of whom own a mobile phone.
Broken down, the 18–24 group tied for first place for smart phone ownership, at 65 percent, with Americans aged 25–29. A slightly lower percentage of kids aged 16–18 reported owning a smart phone — 63 percent. All other age groups came in at 60 percent or lower.
The college-age crowd was somewhat average in ownership of traditional desktops and laptops. Highest home computer ownership was reported among 16- to 17-year-olds, at 93 percent. They were followed by the 30–49 demographic, which came in at 85 percent. Americans aged 18–24 and those aged 25–29 reported home computer ownership of 82 percent, according to the study.
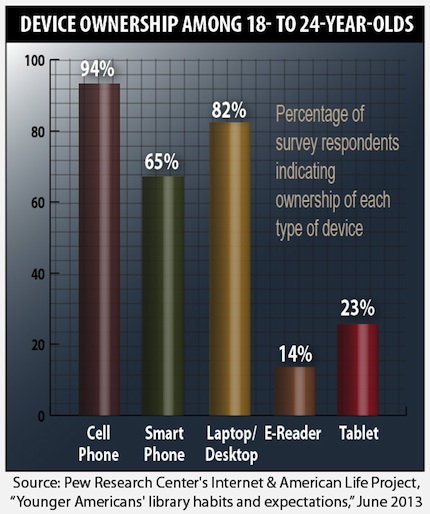
On the tablet front, the 18–24 demographic was again somewhat average. Twenty-three percent reported owning a tablet. That compares with 26 percent of 16- to 17-year-olds and 25- to 29-year-olds, 35 percent of the 30–49 demographic, 19 percent of the 50–64 group, and 15 percent of Americans aged 65 or older.
The one technology in which the 18–24 group seemed the least interested was e-readers. Only 14 percent reported owning an e-reader (tying with the 65-plus group), compared with 21 percent in the 16–17 group, 17 percent in the 25–29 group, 26 percent in the 30–49 group, and 18 percent in the 50–64 demographic.
The latest Pew report was based on a survey of 2,252 Americans aged 16 and older. The research was underwritten by the Bill & Melinda Gates Foundation. Compete details are available in the Pew Internet library research portal at pewinternet.org.