Students Get Hands-On Experience with Open Testbed for Cybersecurity Research
The free, open-infrastructure DETERLab provides exercises for students to learn cybersecurity techniques by getting their arms around attacks and defenses.
- By Dian Schaffhauser
- 11/04/14

Shutterstock.com
Despite the media attention paid to the STEM skills gap that currently exists in government and industry and efforts to lure young people into STEM fields, actually supplying students with hands-on experience is hard — particularly in cybersecurity. Graduates often end up with a much more theoretical understanding about code injection attacks and botnets than with direct observation and interaction.
A project started 10 years ago at the University of Southern California is working to reverse that equation. The Cyber Defense Technology Experimental Research, or DETER Project, runs the DETERLab Education Site, a free resource that enables faculty members from all over the world to use pre-built exercises in their classes, letting students try out security activities in a safe environment.
DETERLab is an advanced testbed facility where researchers and academics conduct cybersecurity experimentation. Currently, 600 researchers in 16 countries use the lab to advance their work in security fields. But 67 different institutions also use the testbed — many of them repeatedly — to run cybersecurity activities as homework or semester-long labs in their computer science courses. And the DETER team says there's plenty of room for more.
What DETERLab Offers
The education initiative started when USC received grants from the National Science Foundation to work with several partner universities in developing the security exercises. Now, DETERLab provides those resources — and the infrastructure to run them on — to instructors in community colleges, state colleges, research universities and even high schools. Students can work through the exercises without breaking or attacking "something for real," said Terry Benzel, principal investigator of the DETER project and deputy director of USC's Internet and Networked Systems division in the School of Engineering.
These real-world activities run the cybersecurity gamut: buffer overflows, man-in-the-middle attacks, worm modeling and detection, denial-of-service and distributed denial-of-service attacks, forensics and monitoring, along with other topics thought up and contributed by people at the schools using DETER. For example, a professor from Washington State University doing work in power grids has developed exercises for securing distributed systems, which, said Benzel, "is really important."
As a DETER Web page explains, each activity is a "packaged experiment." Students create and manipulate an instance of the experiment using a Web-based interface to "request, reconfigure or release lab resources" in order to run an experiment just the way it's written or to pursue their own variations in network setup or computing components.
How DETERLab Works
To gain access to DETERLab, a faculty member fills out an online form with details such as how many exercises the instructor plans to do, how many machines are needed and for what duration. A committee reviews applications and typically gives approval within two or three days, with consideration given to the available computing resources and avoiding conflicts among users. "If 10 faculty members all show up and say they're going to have a huge project due the week before Thanksgiving, we've got a problem," noted Benzel.
DETER runs on a first-come, first-served reservation basis. But the approach isn't fail-safe: Instructors new to the program tend to request far more computing resources than they end up using, noted Benzel. "You ask them, 'How many machines do you need for how many weeks?' They don't know, and they tend to say really big numbers and we reserve those: 'Class CS501 now gets 50 machines.' Well, it turns out they only need three."
Once an instructor has access to the site, he or she creates an educational project in DETERLab and assigns the exercises to the students. Then the students work through the exercises as experiments in the lab. As those activities take place, all network communication is isolated to allow the exercises to run malicious code and perform destructive actions just like it happens in real life — but without the devastation of a data breach, poisoned workstation or malfunctioning network.
Benzel clarified that the lab is "technology oriented, not product oriented." For example, she said, although firewalls are now ubiquitous, built into the home routers, cable services and operating systems we use, setting up a firewall as a newbie system administrator in a corporate or government setting is still "one of the first things you're going to have to deal with." In the DETERLab setting, no specific commercial product is used; it's typically a software simulator running an open source program. "It's not about setting up Symantec's version of a firewall; it's about what the important things are you need to know about firewall configurations — IT and ports and traffic. That's what you learn," she said. "Then when you're in a job setting and your boss has bought somebody's firewall and he wants you to set it up, you know what that terminology is, you know what's involved in setting it up,and, in fact, you've seen how if you didn't set it up correctly, it broke. If you didn't configure a particular port number correctly, an attack came through."
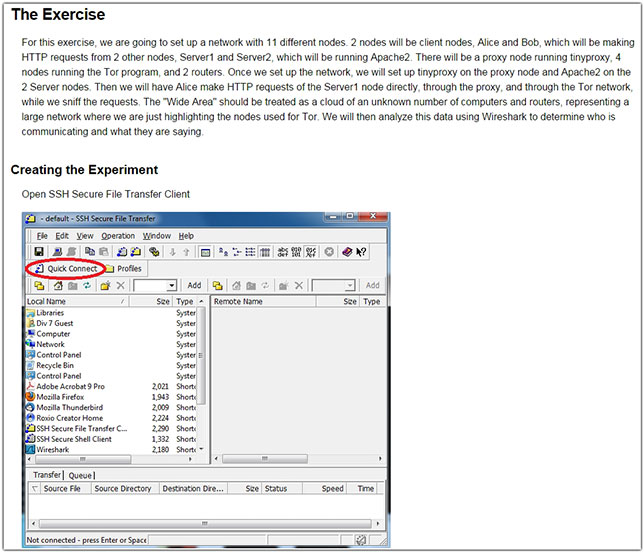
DETERLab's test exercises allow students to work through real-world cybersecurity scenarios in a lab environment.
Faculty Support
Instructors get access to project administration tools that allow them to create and manage student accounts, select and assign exercises, grade exercises, set access controls to limit students' access to others' work and view usage reports for their classes.
When faculty members have problems, DETERLab's support team can help them out. "Let me be clear," Benzel emphasized. "We set things up so that the faculty member or their teaching assistant has to filter all the student questions. I'm not allowing my support staff to get bombarded with questions from lost students. But we're really helpful in making sure the faculty members have what they need. And we're building in more technologies to give monitoring back to the faculty member: Did the student even start? When did he start the homework — midnight the night before it was due?"
The idea behind the monitoring capabilities is to help teachers help their students get through the "learning barrier" earlier in the semester — "any time the student hasn't started working on it because he's blocked or afraid or got lost when he first logged in and he didn't understand some basic concept that he needed to understand," Benzel explained.
She acknowledged that the approach might be both "a little philosophical and idealistic," adding, "We believe that if we can get the student through the learning barrier early in the semester, they are going to be so attracted to this hands-on work; they're going to get in there and do their exercises sooner than the last minute and maybe have the opportunity to do things that weren't even assigned to them."
The Impact of DETERLab
Next up for the lab is to create some "capture-the-flag" exercises to allow students to compete with each other remotely. Two institutions, for example, could have a friendly contest from their own locations. The NSF awarded DETERLab $300,000 to develop the competitions as part of a larger effort that will, according to the grant, "cover a broad range of security topics, such as infrastructure threats and defenses, denial-of-service, botnet detection and infiltration, etc. Competitions will occur multiple times during a semester and will involve students from different institutions, alternating between an attacker and a defender role."
Just as important, the researchers will also address the concept of "ethical defense" through the creation of online materials that students will be quizzed on before they're given access to the competitions.
Other free and fairly open testbeds — GENI, PlanetLab and emulab — exist for computer science research and classroom use. But those others are concentrated on "all-around networking," observed Benzel. DETERLab is the only one focused on security.
The students who have worked through the DETERLab exercises "really know the stuff in a way that's very different, which feeds into the whole question of interactive learning," said Benzel. "They come back to us, because they're getting two and three job offers."
When an interviewer asks a candidate with DETERLab experience, for example, what he or she knows about setting up firewalls, the response goes way beyond trying to recall the process from a chapter in a book, said Benzel. "These kids say, 'I know it! I did it! I built one; I tore it down; and I broke it, and my buddy did this to it.' They have so much enthusiasm and so much real experience in these very tricky cybersecurity areas."