Okta, OpenID Foundation Propose New Identity Security Standard
Okta and the OpenID Foundation have announced the formation of the IPSIE Working Group — with the acronym standing for Interoperability Profiling for Secure Identity in the Enterprise — dedicated to a new identity security standard for Software-as-a-Service (SaaS) applications.
The standard is backed by cloud giants Microsoft and Google, along with many other major industry players.
It was formed, its backers say, because the lack of an identity security standard is causing cybersecurity problems, among which identity is often a prime target or vector. IPSIE integrates key identity management capabilities like single sign-on (SSO), risk signal sharing, and session termination, offering a framework to better secure enterprise applications.
SaaS is tightly associated with cloud computing, of course, and as noted two cloud giants are participating in the project along with other SaaS providers such as Slack and Atlassian. There is no mention anywhere of Amazon or Amazon Web Services (AWS), though the latter works with Okta tech and supports identity federation through OpenID Connect.
Along with the cloud giants, the project is meant to help other identity providers, ISVs and public and private sector organizations integrate identity security across throughout their ecosystems. "In addition to the basics of SSO and MFA, IPSIE will enable organizations to better control governance, entitlements, workflows, authorization, and continuous authentication to detect risk signals effectively and take actions to manage their identity security posture," Okta said in a news release.
The full set of existing and new standards aggregated by IPSIE to support the integration of critical identity security capabilities into SaaS apps includes:
- Single Sign-On: Centralize login, policies, and enforcement
- Lifecycle Management: Secure user on/offboarding and prevent security risks like orphaned accounts and shadow directories to avoid unauthorized access
- Entitlements (Governance/ Privileged Access): Enforce least privilege access and move toward zero standing privileges
- Risk Signal Sharing: Seamless security insights sharing across your entire security ecosystem
- Session Termination: Immediately terminate all user sessions in response to detected threats
The project site says it may also address problems like:
- Discoverability of specific features within the above capabilities
- New user onboarding and account recovery
- Discovering the application used within an enterprise
- Monitoring and provisioning application usage
- Managing restrictions on application usage
"We believe the new, single Identity Security standard being created is an industry game-changer," Okta said in an Oct. 16 blog post. "Open and available to everyone, it has the potential to transform enterprise SaaS security."
To help organizations get started, the company has published, "Preparing for the New Identity Security Standard," which details working with mechanisms like single sign on (SSO) and AuthO, the identity management platform acquired by Okta a few years ago.
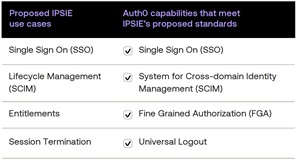 [Click on image for larger view.] AuthO for IPSIE (source: Okta).
[Click on image for larger view.] AuthO for IPSIE (source: Okta).
As shown in the screenshot above, Okta is highlighting how AuthO can help meet the goals of IPSIE.
The company said it has already worked with leading SaaS vendors to build more than 125 deep integrations with many popular enterprise applications coming from Google, Microsoft Office 365, Slack, Atlassian and others.
"Okta will continue working with third-party standards bodies, Identity providers, and independent software vendors to create open, interoperable standardization across Identity security to benefit all organizations," the company said. "The larger the ecosystem, the more secure our industry becomes and the closer we are to free everyone to safely use any technology."
About the Author
David Ramel is an editor and writer at Converge 360.