Report: Identity Has Become a Critical Security Perimeter for Cloud Services
A new threat landscape report points to new cloud vulnerabilities. According to the 2025 Global Threat Landscape Report from Fortinet, while misconfigured cloud storage buckets were once a prime vector for cybersecurity exploits, other cloud missteps are gaining focus.
"Cloud services now sit at the center of modern operations, and identity has become one of the most critical security perimeters," said a post exploring the report from the company's FortiGuard Labs. "Cloud breaches are no longer limited to misconfigured storage buckets. As infrastructure migrates to the cloud, attackers are finding familiar footholds to exploit, such as over-permissioned identities, credential leaks in public code repositories, and lateral movement through cloud-native services.
"FortiCNAPP telemetry shows that attackers often begin by logging in from unfamiliar geographies, sometimes within hours of a developer's legitimate activity. From there, they escalate privileges, establish persistence, and use legitimate services to blend into normal network traffic. In 2024, 25% of all cloud incidents began with reconnaissance, such as API enumeration, permission probing, and discovery of exposed assets."
That telemetry is key to the report, which is based on Fortinet's global sensor network and threat intelligence, and that intelligence suggests the advantage enjoyed by threat actors is growing, and will continue to do so until organizations change how they measure and manage risk.
One of the report's key findings, "Cloud attacks are evolving, but misconfigurations still reign," discusses the above finding in greater detail.
"Cloud environments remain a top target, with adversaries exploiting persistent weaknesses, such as open storage buckets, over-permissioned identities, and misconfigured services," the report said. "Lacework FortiCNAPP telemetry shows a steady rise in cloud compromises, often involving identity abuse, insecure APIs, and privilege escalation. These vectors are frequently combined in multi-stage attacks that leverage automation and legitimate services for stealth and persistence. Reconnaissance remains the most prevalent tactic, with attackers probing APIs, enumerating permissions, and scanning for exposed assets. In 70% of observed incidents, attackers gained access through logins from unfamiliar geographies, highlighting the critical role of identity monitoring in cloud defense."
 [Click on image for larger view.] Evolving Threat Landscape (source: Fortinet).
[Click on image for larger view.] Evolving Threat Landscape (source: Fortinet).
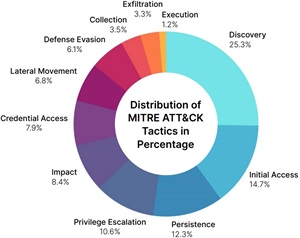
The MITRE ATT&CK tactic distribution chart above shows some key takeaways of its own:
- Discovery (25.3%): The most common tactic in cloud attacks, indicating widespread scanning, enumeration of permissions, and probing of APIs and services.
- Initial Access (14.7%): Attackers most often gain entry through leaked or stolen credentials, phishing, or misconfigured authentication settings.
- Persistence (12.3%): Adversaries create or modify cloud identities and roles to maintain long-term access to compromised environments.
- Privilege Escalation (10.6%): Attackers manipulate permission policies or exploit cloud APIs to elevate their access rights.
- Impact (8.4%): Activities aimed at disrupting services, tampering with data, or initiating ransomware-like attacks in the cloud.
- Credential Access (7.9%): Techniques used to extract keys, passwords, or tokens for lateral movement or further exploitation.
- Lateral Movement (6.8%): Movement between cloud services, regions, or accounts after initial compromise, often undetected.
- Defense Evasion (6.1%): Methods used to avoid detection, such as using legitimate services or hiding malicious behavior in normal workflows.
- Collection (3.5%): Gathering sensitive data or metadata for later use or exfiltration.
- Exfiltration (3.3%): Stealing data from cloud storage, databases, or containers, often through abused APIs.
- Execution (1.2%): Running malicious scripts or binaries, typically through Bash, PowerShell, or Python in cloud workloads.
The report underscores that reactive cloud security is no longer viable and advises organizations to invest in:
- Proactive exposure management;
- Automation; and
- Identity- and API-centric defenses to stay ahead of attackers who now operate at machine speed using automation, AI, and CaaS ecosystems.
Getting more specific, advice for cloud protection is summarized here:
- Adopt a Zero Trust Mindset:
- Treat every identity, device, and API call as potentially hostile.
- Assume breach and verify explicitly before granting access.
- Enforce least privilege access across all cloud assets.
- Improve Identity and Access Management (IAM):
- Monitor for logins from unfamiliar geographies -- seen in 70% of cloud compromises.
- Audit and restrict over-permissioned IAM roles and policies.
- Secure secrets and credentials, especially those in public code repositories like GitHub.
- Secure Cloud APIs:
- Recognize APIs as a top vector for lateral movement and privilege escalation.
- Implement strong security controls: rate limiting, auth/authz, monitoring.
- Guard against Cloud Instance Metadata API Exploitation (T1556.004).
- Strengthen Cloud Workload Protection:
- Protect cloud VMs, containers, and Kubernetes clusters from persistent threats.
- Watch for:
- Command Execution (T1059)
- C2 via Web Services (T1102)
- Resource Hijacking (T1496) for cryptojacking
- Deploy Continuous Threat Exposure Management (CTEM):
- Continuously monitor your attack surface.
- Simulate real-world attacks using red/purple teaming and adversary emulation.
- Use EPSS and CVSS to prioritize patching.
- Implement Breach and Attack Simulation (BAS) to validate defenses.
- Automate Detection and Response:
- Use AI/ML to detect unusual API behavior and automate alerts.
- Integrate with response systems to reduce time-to-containment.
- Monitor the Darknet and External Exposure:
- Watch for leaked credentials and cloud-focused threats on hacker forums.
- Track newly deployed adversary infrastructure (e.g., phishing domains).
- Simulate and Harden Against Real-World Scenarios:
- Run adversary emulation using MITRE ATT&CK frameworks.
- Focus on cloud-relevant techniques like:
- Valid Accounts (T1078)
- Exploit Public-Facing Application (T1190)
- Scheduled Task/Job (T1053)
Besides cloud threats, other key takeaways of the report include:
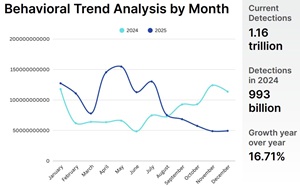
- Automated Reconnaissance Is Surging:
- Attackers are using automated tools to scan the internet at massive scale — up to 36,000 scans per second — to quickly identify vulnerable services before defenses are in place.
 [Click on image for larger view.] Behavioral Trends (source: Fortinet).
[Click on image for larger view.] Behavioral Trends (source: Fortinet).
- AI Is Powering the Cybercrime Supply Chain:
- AI tools like FraudGPT and ElevenLabs are automating phishing, malware creation, and impersonation, enabling more convincing and scalable cyberattacks.
- Credential Theft and Access Brokerage Are Booming:
- Credential theft rose by 500% in darknet forums, driven by infostealers and Initial Access Brokers selling enterprise logins at scale.
 [Click on image for larger view.] Top APT Adversaries (source: Fortinet).
[Click on image for larger view.] Top APT Adversaries (source: Fortinet).
- Ransomware Groups Are Fragmenting but Still Powerful:
- While 13 new ransomware groups emerged, just four accounted for 37% of all attacks, showing both diversity and concentration in the threat landscape.
- Exploitation Is Increasing in Volume, Not Speed:
- The time to exploit new vulnerabilities remains steady, but attackers launched over 97 billion exploitation attempts in 2024 alone, thanks to automation.
- Post-Exploitation Tactics Are Growing Stealthier:
- Adversaries use built-in tools like PowerShell, WMI, and Active Directory features to persist within systems while avoiding traditional detection.
- IoT Devices Are a Prime Exploitation Target:
- More than 20% of exploitation attempts targeted vulnerable IoT devices like routers and cameras, often due to weak credentials and poor patching.
- RDP Remains a Key Vector for Lateral Movement:
- Remote Desktop Protocol was involved in 88% of lateral movement cases, making it a top method for attackers to move across internal networks.
- Darknet Markets Are Fueling Cybercrime-as-a-Service:
- Cybercriminals of all skill levels can now buy credentials, malware, and exploits from darknet marketplaces, driving scale and sophistication of attacks.
- Hacktivists Are Merging With Cybercriminal Tactics:
- Hacktivist groups increasingly use ransomware and data leaks to further ideological goals, blending activism with financially motivated cybercrime.
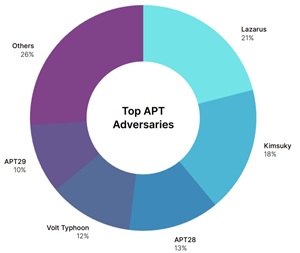
- Nation-State Actors Remain Active and Sophisticated:
- Advanced Persistent Threat (APT) groups from China and Russia continue to target government, education, and tech sectors with coordinated cyber espionage campaigns.
- Attackers Exploit Trusted Tools and Encrypted Channels:
- Common utilities like scheduled tasks and encrypted DNS/SSL are abused to hide C2 traffic and maintain stealthy access inside compromised networks.
- Legacy Vulnerabilities Still Pose a Major Threat:
- Old but unpatched flaws — like Log4Shell and SMB vulnerabilities — remain popular targets due to persistent gaps in basic cyber hygiene.
The 2025 Fortinet Global Threat Landscape Report is based on global telemetry collected by FortiGuard Labs through Fortinet security products, including firewalls, NDR, and cloud protection platforms. It combines real-world intrusion data, darknet monitoring, and cloud workload analysis, with all threat activity mapped to the MITRE ATT&CK framework. The report tracks attacker behaviors, exploits, and emerging trends across diverse sectors and geographies to provide a comprehensive, data-driven view of the evolving threat landscape.
The full report is available on the Fortinet site here (registration required).