Data Leaks from Education Ransomware Attacks Doubled in 2021, CrowdStrike Says in Global Threat Report
- By Kristal Kuykendall
- 02/15/22
A new report released today by cybersecurity intelligence experts at CrowdStrike revealed that ransomware-related data leaks rose 82% in 2021, as cybercriminals are increasingly focusing on three areas: endpoints and cloud workloads, identity, and data.
In all, CrowdStrike Intelligence observed 2,686 data leaks related to ransomware attacks in 2021, compared to 1,474 the year prior. Ransomware attacks targeting the education sector led to 105 data leaks in 2021, just over double the 52 reported in 2020.
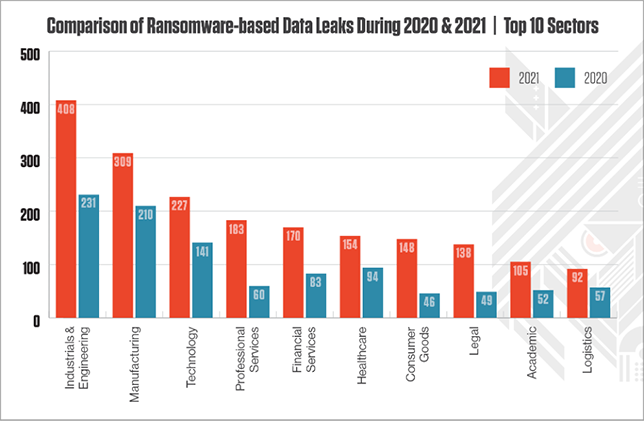
In its 2022 Global Threat Report, CrowdStrike warned that cyberattacks are “moving beyond malware” and increasingly “living off the land,” or using legitimate credentials and built-in tools to access their victims’ networks. Of all the detections indexed by CrowdStrike Security Cloud in the fourth quarter of 2021, the report said, 62% of them were malware-free, “exploiting stolen user credentials and identity to bypass legacy security solutions.”
“In the face of massive disruption brought about by the COVID-driven social, economic and technological shifts of 2020, adversaries refined their tradecraft to become even more sophisticated and brazen,” CrowdStrike CEO George Kurtz said in the report’s executive summary. “The result was a series of high-profile attacks that rocked many organizations and, on their own, represented watershed moments in cybersecurity.”
The company said it observed an average of more than 50 ransomware events per week in 2021. It noted a growth in interactive intrusion campaigns over 2020, a marked increase in attacks targeting cloud-based services, and a vast, evolving “eCrime” ecosystem targeting larger victims for greater financial gain.
The Global Threat Report reviews the top cyberattack adversaries used in 2021; it introduces two new threats dubbed “Wolf” and “Ocelot”; and it deep-dives into case studies featuring attacks using Wizard Spider, Nemesis Kitten, Panda, and Prophet Spider.
The report also outlines new operations and techniques from Iran, China, Russia and North Korea, and it breaks down the aftermath of the disruptive Log4Shell attacks from December 2021.
CrowdStrike’s report closes with the following recommendations for cybersecurity professionals:
- Protect all workloads
- Know your adversary
- Be ready when every second counts
- Adapt a Zero Trust model
- Monitor the criminal underground
- Eliminate misconfigurations
- Invest in elite threat hunting
- Build a cybersecurity culture
Find the full report and learn more at CrowdStrike.com.
About the Author
Kristal Kuykendall is editor, 1105 Media Education Group. She can
be reached at [email protected].