ABI Research recently released a startling statistic: Malware targeting IoT devices climbed 700% during the pandemic.

The agenda for the 2023 Tech Tactics in Education conference has been revealed. The inaugural event will offer five tracks — two for K–12, two for higher education, and one for both — spotlighting data and IT security in the "new now."

A new guide for higher education from Ninjio on improving cyber defense through campus-wide training offers actionable advice for institutions’ leaders on how to translate their core competency — education — into a successful cybersecurity awareness program that reduces vulnerabilities and improves security posture across the entire campus and network.
Screen-casting and collaboration provider Airtame has expanded its partnership with unified communications and digital signage software developer Rise Vision to expand education institutions' ability to display emergency alerts and school messaging on Airtame-connected devices across entire campuses, according to a news release.
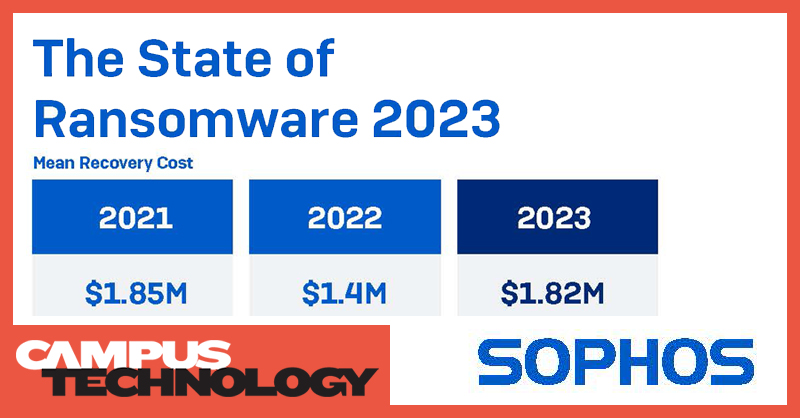
Nearly eight out of 10 higher ed organizations surveyed for Sophos’ 2023 State of Ransomware Report said they were hit by ransomware last year — a 23% increase from the previous year’s results — making education the most-attacked sector in 2022.
Managed services provider Apogee has introduced Cloud and Security Professional Services, offering expertise, tools, and processes to accelerate cloud adoption and strengthen an institution's security posture.

Gartner has identified six critical areas where the use of large language models such as ChatGPT can present legal or compliance risks that enterprise organizations must be aware of — or face potentially dire consequences. Organizations should consider what guardrails to put in place in order to ensure responsible use of these tools, the research firm advised.

The University of South Carolina Aiken recently found a creative way to staff a new security operations center — and give students hands-on cybersecurity training at the same time. We spoke with Ernest Pringle, vice chancellor for IT and CIO at USC Aiken, about creating a student-led SOC, helping students put cybersecurity theory into practice, forging regional cybersecurity partnerships, and more.
Nonprofit organization Women in Cybersecurity has partnered with the Information System Security Certification Consortium, aka (ISC)², to launch a new Certified in Cybersecurity Certification Summer Camp.

A majority of chief information security officers in the U.S. education sector believe they’re likely to experience a material cyber attack in the next 12 months, and a majority have dealt with a material loss of sensitive data in the previous 12 months, according to the newest Voice of the CISO report published this week by cybersecurity company Proofpoint.